February 8, 2024

Networking Nirvana: Crafting Robust Applications with Linux Networking Skills
February 3, 2024
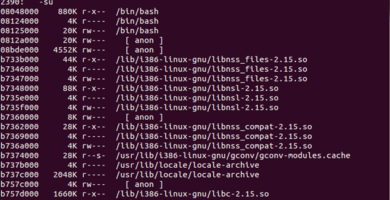
Using Pmap to Report Memory Map of a Process (With Examples)
February 2, 2024

How to hire a cyber security developer to protect your business
February 2, 2024

Best VPNs for Linux with and without GUI
February 2, 2024

Compare NetSuite and Red Hat Enterprise Linux
February 2, 2024